“We operate in a zero-trust environment.”
In our globally connected economy, cybercriminals specifically look for weak points in value chains and use them as a gateway, for data theft and blackmail. At the same time, the cyber skills gap is growing, warns Gretchen Bueermann, Knowledge Lead at the WEF. What are we facing?
Gretchen, in the WEF‘s flagship report, you examine the cybersecurity trends that will affect economies and societies in the years ahead. Which are the most important developments?
Firstly, I think that the way we approach the governance of emerging technologies is going to be critical. We have the opportunity to learn from past experiences and develop regulations and policies related to things like generative artificial intelligence (AI) that are truly secure by design.
A more proactive approach than in the past is essential given the dual-edged nature of AI, which can be used for both defensive and offensive cyber activities. By establishing robust, forward-thinking policies, we can mitigate the risks, or at the very least, clearly identify the risks associated with these technologies before they become widespread issues.
Moreover, as we work to develop common governance strategies and policies, we will see a shift of the burden of security away from the consumer, the everyday users of this technology, where it has ultimately landed with other technological developments.
This involves creating more resilient systems and ensuring that security measures are built into the technology from the ground up. By doing so, we can protect consumers without requiring them to have specialized knowledge or take extensive actions to safeguard their data.
Lastly, something that is perpetually at the top of the critical issues list is the growing need to address the cyber skills and talent shortage. The cybersecurity landscape is evolving rapidly, and the demand for skilled professionals is outpacing supply. An extensive new Korn Ferry report finds that by 2030, more than 85 million jobs could go unfilled because there aren’t enough skilled people to take them.

This shortage impacts the ability of organizations to respond to cyber incidents or adapt to new developments in the landscape like generative AI, not to speak of their basic ability to maintain robust security postures. Investing in education and training programs is essential to build a capable workforce that can handle emerging cyber threats, but we also have to move beyond that to more creative solutions to drive interest in the industry, and to train workers outside of traditional credentialing systems.
The main concern we have about this is the growth rate of cyber inequity.
The cybersecurity economy grew exponentially faster than the overall global economy in 2023, and even outpaced growth in the tech sector. Are we on the right track?
It is no secret that the cybersecurity industry continues to grow. Especially as we continue to experience the knock-on effects of a shift to more remote work, and an Internet of Things (IoT) environment that sees more devices becoming engaged with end-consumers every day. The main concern we have about this is the growth rate of cyber inequity. This includes an increasing divide between cyber-resilient organizations and those struggling to maintain basic levels of cyber resilience. By cyber resilience, I am referring specifically to an organization’s ability to anticipate, withstand, recover from, and adapt to a cyber attack.
Small and medium-sized enterprises (SMEs) are particularly vulnerable; we see the number of SMEs maintaining minimum viable cyber resilience down by 31 percent since 2022, exacerbating the disparity between large and small organizations.
Industry growth rates like the ones we’ve been experiencing are only a net positive if we can find creative solutions to check this widespread disparity, because, at the end of the day, the SMEs that are struggling to maintain this minimum level of cyber resilience, are all an integral part of the supply chain and ecosystem of their larger “more resilient” counterparts. So to some extent, the security weakness they experience has an upstream effect that really shouldn’t be ignored.
Approximately half of experts surveyed agree that generative AI will have the most significant impact on cybersecurity in the next two years.
The rapid spread of generative AI and other new technologies that can easily be used by cyber attackers poses a serious threat both for business and in public life. What are the scenarios, and how can we best prepare?
This was a particularly interesting topic to speak to our experts about this year because in general from the cyber perspective they took a relatively pessimistic posture. Fewer than one in ten respondents reported that they believe that in the next two years generative AI will give the advantage to defenders over attackers.
And approximately half of experts surveyed agree that generative AI will have the most significant impact on cybersecurity in the next two years. This is a particularly interesting problem to tackle in the short to medium term, because adversarial and malicious groups are not governed by regulations, legal teams or boards that advise on proper use of new technologies, so their scope to experiment with new attack vectors or methods is considerably wider than a defender operating within the legal and ethical parameters of their organization.

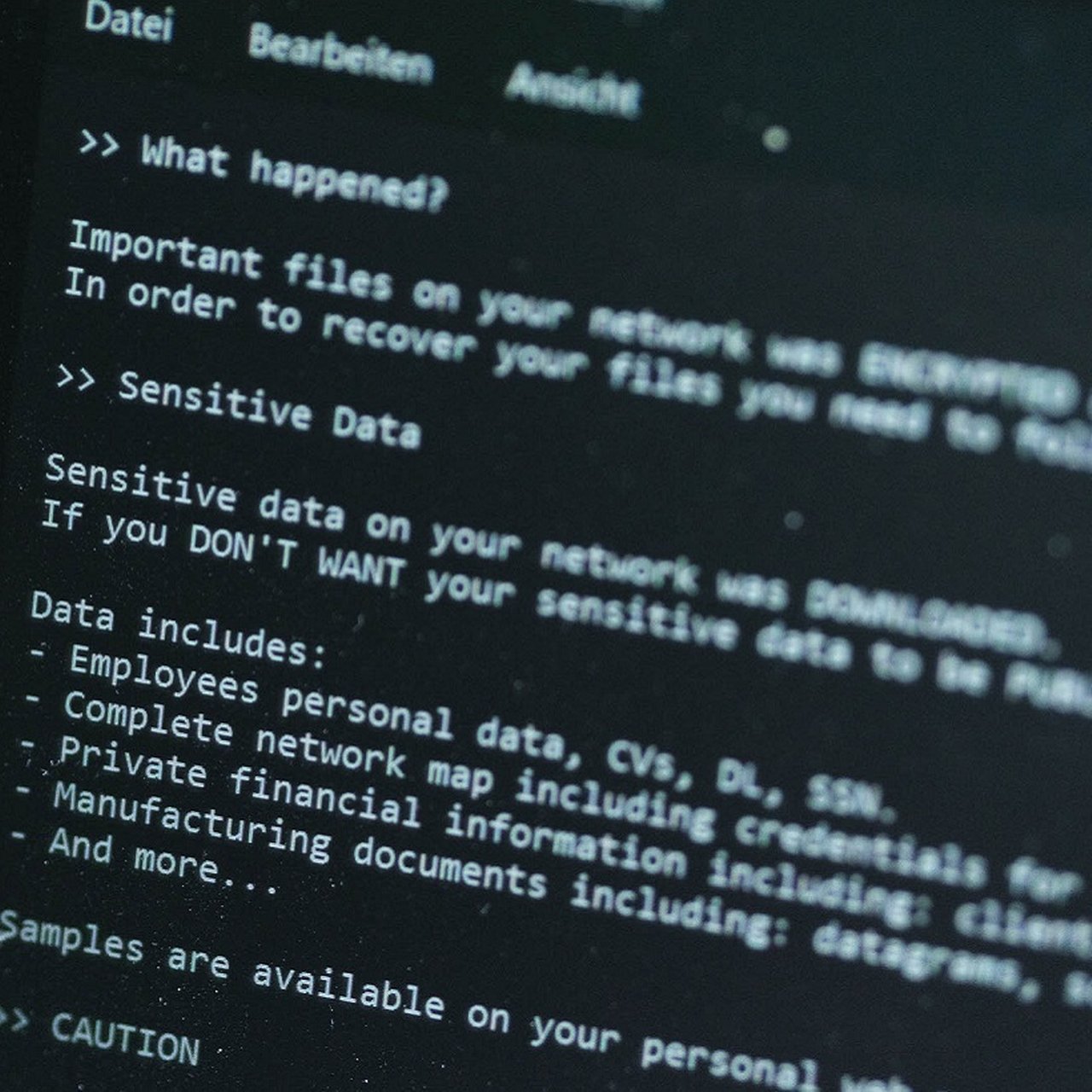
One of the most interesting scenarios to us is the way we’ve seen deep fakes used to interfere in Government elections and private corporations. As an example, in August 2023, a software company fell victim to an incredibly advanced and complicated social engineering attack, which used AI to create a deepfake audio of an employee. The attackers sent the employees a fake SMS (a smishing attack) about open enrolment for company health insurance. One employee clicked on the link in the SMS and provided their credentials to the fake system. Immediately after the attacker received the credentials, they called the employee’s phone to retrieve the multifactor authentication (MFA) code.
This is perhaps where the story might have ended in a pre-deep fake landscape, as I think we’ve all been trained not to give out sensitive security information to strangers over the phone. However, in this scenario, because of the attacker using a deepfake audio of a familiar colleague, the employee ignored their suspicions and provided the requested information to the attacker. This allowed the attacker to gain approval from the authentication systems used by the victim organization.
Part of our task is to help employees and leaders alike to understand that we now operate in a zero-trust environment both online and offline.
This is just one scenario, and in recent months we’ve seen a variety of leaders (including CEOs) fall victim to these types of attacks. Part of our task is to help employees and leaders alike to understand that we now operate in a zero-trust environment both online and offline (zero trust security means that by default no one is trusted from inside or outside the network, and verification is required from everyone trying to gain access to resources on the network). We need to grapple with the fact that some of the emerging cybersecurity problems may need to have person-centric solutions to complement technical solutions that go beyond traditional security answers.
You state that cyber inequity is widening globally as well as within societies, and that creative action is needed to address the growing cyber-skills gap. Do you have an example?
This is a great question because I think there are a number of creative ways to think about this problem. And make no mistake, this is a major issue. In the UK alone, research shows that 43 percent of UK SMEs have been unable to hire cybersecurity support due to the shortage of specialists or challenges in attracting, recruiting and retaining cybersecurity practitioners.
I think the first thing to do is to understand the difference between a true lack of skilled labour in this sector, and a gap in the ability of the industry to efficiently (re)deploy and retain the existing talent.
I think the first solution that I’ve seen implemented very successfully across a variety of organizations is to upskill existing workers from non-traditional backgrounds. The cost of taking an existing staff member with an aptitude for cyber and helping them to upskill and then placing them in the organization to gain practical experience can often be considerably lower than the process of recruiting and training a new employee.
The cyber industry on the whole has an issue when it comes to attracting and retaining women.
The other thing that I want to point out is this issue of retention, especially when it comes to women in cyber. The cyber industry on the whole has an issue when it comes to attracting and retaining women. Encouraging more women to enter and thrive in cybersecurity roles helps to broaden the talent pool and brings diverse perspectives to the field, which is crucial for innovative problem-solving.
Organizations like Women4Cyber, a non-profit European private foundation, aim to promote, encourage, and support the participation of women in cybersecurity by offering mentorship, networking opportunities, and career development resources. We need more organizations like this in the industry in order to break out of the pattens and trends that have plagued us for the last decades.
Ultimately, addressing the widening cyber inequity requires a multifaceted approach, which includes specific attention to three core components:
- Upskilling existing workers from non-traditional backgrounds as a cost-effective way to fill cybersecurity roles.
- Focusing on the retention and advancement of women – and cyber professionals from the global south, of course – in order to continue diversify the talent pool and foster innovation.
- Leveraging public-private partnerships for education and training programs to help ensure a steady pipeline of skilled professionals.

Even if a company manages to protect itself in the best possible way, it still needs to understand the vulnerability of its supply chain. So can we ever reach cyber resilience without having the entire cyber ecosystem in mind?
You cannot have one without the other. As we put together this year’s report, we thought a lot about what key indicators for systemic cyber resilience are, and how they make up both cyber resilience at the organizational level, but also industry-wide and national resilience.
These types of key indicators include things like the quantity and quality of industry collaborations, the effectiveness and clarity of regulations, the maturity and accessibility of the cyber insurance market, and the extent to which organizations understand cyber risk coming from their own supply chains and third-party relationships.
There is no cyber resilience without ecosystem awareness.
This year, we were particularly struck by the findings that 41 percent of organizations that suffered a material impact from a cyberattack said it originated from a third party, and yet many of our respondents report not knowing very much about the cybersecurity of their supply chain partners. This is the equivalent of investing heavily in a fancy lock for your front door, but giving the key to anyone who might need access to your home, regardless of your knowledge of them. To me, there is no cyber resilience without ecosystem awareness.
In your report, you define digital security as a strategic imperative and say that its reinforcement is only achievable through public-private action. What could this look like?
Let me give you three examples of places where progress through public-private action creates avenues for progress that would be otherwise impossible. The first is this concept of “threat intelligence sharing”, something we currently do via our Cybercrime Atlas.
Establishing platforms for real-time information sharing between government agencies and private companies is essential. For example, Cybercrime Atlas community members collaborate to map the cybercrime landscape, specific criminal operations, networks, and infrastructure. They then facilitate the disruption of cybercriminal activities by providing actionable research to its members.
We’ve also spoken a lot about cybersecurity education and the skills gap, which clearly cannot be addressed by one organization or government. Public-private partnerships can help to co-create cybersecurity training programs to address the skills gap. Initiatives like the Cybersecurity Talent Initiative in the US recruit and train cybersecurity professionals through public and private sector roles.
We need cooperation across the public-private divide, across sectors, and across countries.
And finally, developing joint cybersecurity standards and frameworks, and avoiding redundant or conflicting regulations, by definition requires cooperation across the public-private divide, across sectors, and across countries. Developing and promoting common cybersecurity standards and frameworks through collaboration has been shown to make security practices across industries more efficient and improve outcomes. A good example is the NIST Cybersecurity Framework, created in partnership between the public and private sectors, which is now a ubiquitous tool across the industry.
You say systemic resilience is not only the most pressing requirement, it is the greatest responsibility. So whose main responsibility is it?
I love this question because I think the answer is in the question itself. Systemic resilience in cybersecurity is really only accomplishable through a truly shared responsibility that spans multiple stakeholders, including governments, private sector organizations, and individual users.
For example, while we rely on governments to create cohesive and comprehensive regulatory frameworks, international cooperation is key for learning and development, and prevention of conflicting norms across countries. When it comes to things like making progress in the fight against cybercrime, private organizations must work to develop viable and scalable methods of information sharing to improve collective defenses. Collaboration between governments and private organizations can also help to address the growing issue of cyber inequity, where civil society can help to facilitate knowledge transfer between large cyber resilient organizations and smaller organizations.
While systemic resilience is clearly a collective responsibility, the greatest responsibility lies with those who have the most influence and resources to implement effective cybersecurity measures, and to help establish cyber norms. Close collaboration between all stakeholders is essential if we hope to make meaningful progress toward a more secure and resilient digital environment.
This interview was conducted by Maike Tippmann. 07/2024.

About Gretchen Bueermann
Gretchen is the knowledge lead at the World Economic Forum’s Centre for Cybersecurity, where her primary focus is cyber frontiers and digital cooperation. She is the author of the annual Global Cybersecurity Outlook Report and serves as the Council Manager of the Global Future Council on Cybersecurity.
Prior to her current role, Gretchen contributed as a data scientist at the International Organization for Migration (UN Migration), co-leading the Data Science and Ethics Group, with a focus on predictive analytics and privacy in humanitarian emergencies. She has also contributed to research at the Behavioral Science Research Lab at the Yale School of Management. Gretchen earned her Master of Arts in International and Development Economics from Yale University.

Maike Tippmann
… is responsible for digital communications projects in Deutsche Bank‘s Newsroom. Since her account with an online retailer was hacked and she paid for several laptops that she had never ordered, she has taken the topic of cyber security very seriously. And yet, time and again, she finds herself almost falling for well-camouflaged attacks.
Recommended content
Digital Disruption | Insights
The convenience of digital banking with the assurance of security The convenience of digital banking with the assurance of security
Cyber expert Pinakin Dave explains why cybercrime is on the rise and how his company "OneSpan" is helping reduce risks to consumers and keep financial transactions safe.
Digital Disruption | Photo Story
“The attack brought us closer” “The attack brought us closer”
The attackers hit shortly before Christmas. How our client, office supply store Schäfer Shop, got business back up and running after having fallen victim to a cyber attack.
Digital Disruption | Insights
How bug bounties are safeguarding cyberspace How bug bounties are safeguarding cyberspace
Ethical hackers conduct test attacks on behalf of companies, which proves to be an indispensable service towards protection against cyber crime.